
What is ModSecurity, often referred to as ModSec, is an open-source web application firewall (WAF) module that can be deployed with the Apache, Nginx, or IIS web servers.
Its primary purpose is to enhance the security of web applications by protecting them from various attacks, including SQL injection, cross-site scripting (XSS), and other common web exploits.
What is ModSecurity? It’s a toolkit designed for real-time web application monitoring, logging, and access control. If it sounds complex, don’t worry. Anyone with experience of ModSecurity will attest that it’s a flexible toolkit, with no hard and fast rules telling you how you should use it.
Generally, ModSecurity leaves you free to decide how you take advantage of the features available instead. This flexibility is a core element of ModSecurity’s identity, and complements its open source structure. In fact, you can enjoy complete access to its source code, which empowers you to customize the tool to suit your unique needs.
And that’s crucial for anyone who wants tools to enable them to achieve what they have to with minimal restrictions. Which is probably all of us, right? ModSecurity is a versatile creation ideal for numerous usage scenarios.
What is ModSecurity – Here’s a brief overview of how ModSecurity works and how to use it:
How ModSecurity Works:
- Request Processing:
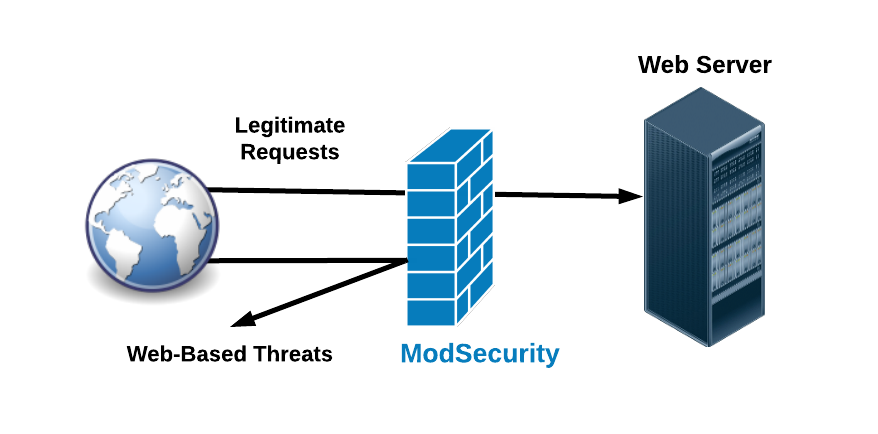
- ModSecurity operates during the request processing phase of a web server. It examines incoming HTTP requests and their associated data.
- Rule-Based Detection:
- ModSecurity uses a set of rules to analyze the incoming traffic. These rules define patterns and characteristics of known attack patterns. When it detects a request that matches these patterns, it can take action to block or log the request.
- Action Handling:
- Depending on the configuration, ModSecurity can take various actions when it identifies a potential threat. Common actions include blocking the request, logging information about the request, or modifying the request to neutralize the threat.
- Response Processing:
- ModSecurity also works during the response processing phase. It can inspect outgoing responses for sensitive information and make additional security-related adjustments if necessary.
What is ModSecurity
- ModSecurity also works during the response processing phase. It can inspect outgoing responses for sensitive information and make additional security-related adjustments if necessary.
How to Use ModSecurity:
- Installation:
- Install the ModSecurity module for your specific web server (Apache, Nginx, or IIS). The installation process may vary depending on your server and operating system.
- Configuration:
- Configure ModSecurity by creating or editing its configuration file. The configuration file typically includes settings for rule management, logging, and other options. You can customize rules based on your specific security needs.
- Rule Sets:
- ModSecurity relies on rule sets to identify and block malicious traffic. You can use the default rule set or choose from various community and commercial rule sets available. Rule sets define patterns and behaviors associated with known attack vectors.
- Logging and Monitoring:
- Configure logging to keep track of detected threats and potential false positives. Monitoring ModSecurity logs is essential for understanding the nature of attacks and adjusting rules as needed.
- Fine-Tuning:
- Fine-tune ModSecurity based on your application’s specific requirements. This may involve adjusting rule parameters, whitelisting known safe traffic, or customizing the handling of specific types of requests.
- Testing:
- Before deploying ModSecurity in a production environment, it’s advisable to thoroughly test its configuration to ensure that it doesn’t inadvertently block legitimate traffic. Adjust rules and settings as needed during the testing phase.
- Maintenance:
- Regularly update ModSecurity and its rule sets to stay protected against the latest security threats. Monitor logs for any unusual patterns and adjust the configuration accordingly.
Keep in mind that ModSecurity is a powerful tool that requires careful configuration to balance security and functionality. It’s recommended to have a good understanding of web application security principles before implementing and configuring ModSecurity in a production environment.
